At last month’s Black Hat security conference in Las Vegas, University of Luxembourg researcher Ralf-Philipp Weimann demonstrated a security weakness related to GPS that could potentially be used by hackers to hijack most modern smartphones. The loophole specifically affects phones that use assisted GPS (A-GPS).
At last month’s Black Hat security conference in Las Vegas, University of Luxembourg researcher Ralf-Philipp Weimann demonstrated a security weakness related to GPS that could potentially be used by hackers to hijack most modern smartphones. The loophole specifically affects phones that use assisted GPS (A-GPS).
Many modern smartphones now come with a GPS receiver to allow navigation features and other location based services. GPS receivers can consume a large amount of battery power if used constantly however; so many phones will employ a system known as assisted GPS to provide an approximate location.
A-GPS uses data transmitted from cell phone towers to triangulate a phone’s position, and while it is not quite as accurate as true GPS it can provide better battery performance when used in conjunction. It is also much quicker at determining a location than GPS which can take anywhere up to 12 minutes to calculate co-ordinates.
The security flaw highlighted by Weimann relates specifically to the use of A-GPS in phones. When a phone sends A-GPS data to cell phone masts to calculate its location it does so over an insecure connection that could easily be intercepted by hackers.
A hacker could switch the A-GPS data being sent from a phone network with its own data, allowing the hacker to determine the location of the phone. The phone could be configured to send this data every time that it requests A-GPS support, so the attacker would no longer need to be in range of the compromised phone to obtain location data.
Weimann stated, “If you just turn it on once and connect to that one network, you can be tracked any time you try to do a GPS lock. This is rather nasty.”
The vulnerability was demonstrated by Weimann on a number of Android phones. While the security hole could potentially result in some rather insidious data theft, Weimann also stated that the problem was pretty easy to solve, but that many manufacturers simply hadn’t bothered to implement the technology to prevent such attacks.
Along with the theft of location data the security flaw could allow for some more serious crimes involving these phones. The A-GPS system is processed on the phone’s main processor rather than the GPS chip, and messages sent by the hacker on the compromised connection could cause system crashes that would allow the hacker to gain remote access to the device.
While it is not thought that anyone has actually exploited this loophole so far it does raise serious concerns over the security of modern smartphones. Malware is a relatively minor problem on smartphones compared to desktop computers as it is much more difficult to get the malware onto devices. The loophole identified by Weimann, and similar potential loopholes, could make smartphones a much more enticing target for professional malware developers in future. Now that this A-GPS loophole has been identified it will most likely be patched on future devices and software updates, but for the time being many smartphones remain vulnerable.
Simon writes for Best Mobile Contracts, a UK mobile phone comparison website.
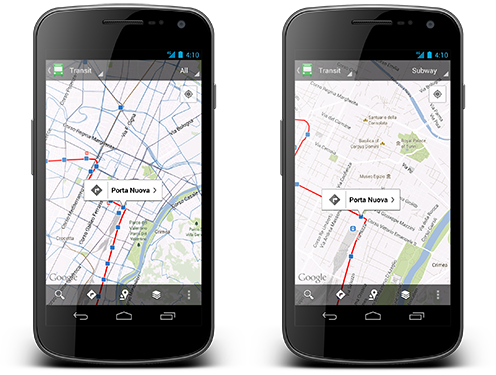 Starting from 2005 Google has collaborated with hundreds of transit authorities around the world to make a unique resource for millions of riders to find out which bus, train, subway or tram can take them to their next destination.With the latest update in Google Maps for Android, Mountain View giant announced to cover public transportation schedules for more than one million transit stops worldwide, in nearly 500 cities world-wide.
Starting from 2005 Google has collaborated with hundreds of transit authorities around the world to make a unique resource for millions of riders to find out which bus, train, subway or tram can take them to their next destination.With the latest update in Google Maps for Android, Mountain View giant announced to cover public transportation schedules for more than one million transit stops worldwide, in nearly 500 cities world-wide.