The Global Navigation Satellite System (GNSS), encompassing GPS, Galileo, GLONASS, and BeiDou, is the engine powering modern geospatial operations, spatial analytics, agriculture automations, infrastructure maintenance, telecoms and banking. For the global community, the reliable integrity of Positioning, Navigation, and Timing (PNT) is non-negotiable. However, targeted interference, once a rare curiosity, has evolved into a recurring operational hazard that can degrade the quality of location and timing data.
Adversaries or careless users employ two primary methods to compromise GNSS accuracy: spoofing and jamming.
Understanding the Threat: Jamming vs. Spoofing
| Attack Type | Technical Mechanism | Geospatial Impact |
| Jamming | A jammer transmits a strong signal within the same frequency band as GNSS satellites. Because real satellite signals reaching Earth are extremely weak, even a low-power local transmitter can significantly raise the noise floor, preventing a receiver from acquiring or tracking satellites. | The effect is data denial. The GNSS receiver either reports low-quality fixes or fails to provide position or time data entirely, potentially halting remote sensing missions or critical PNT-dependent processes. |
| Spoofing | The attacker transmits counterfeit satellite signals that precisely mimic real GNSS signals but carry false timing or position data. Advanced spoofers carefully shape the signal timing and power to “capture” the victim receiver without triggering immediate alarms. | This attack misleads navigation systems. The receiver accepts the forged signals as authentic, reporting a subtly or dramatically incorrect location or time. Spoofing is often harder to detect than jamming. |
GNSS Jamming vs. Spoofing by Geoawesome
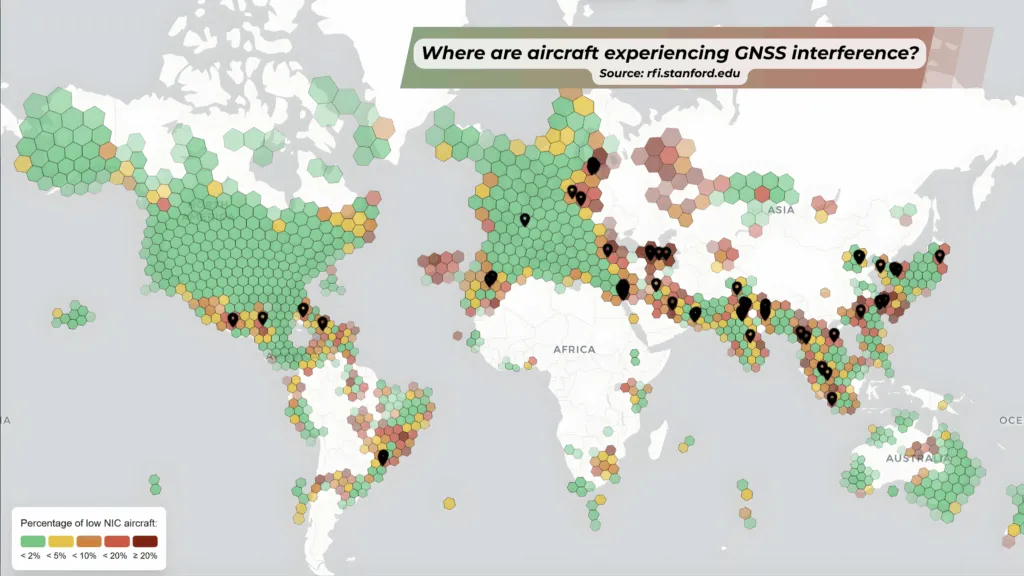
Global Hotspots: Where Data Integrity is Most at Risk
For those processing EO data or deploying assets globally, understanding the spatial distribution of GNSS interference is crucial. Open monitoring initiatives convert datasets, such as aircraft GNSS performance (ADS-B), into spatial heatmaps that quantify the extent of the interference.
Current monitoring shows interference is not uniformly distributed, revealing three key patterns:
- Conflict and Near-Conflict Zones: Persistent, high rates of both jamming and spoofing are frequently observed around the Baltic, Black Sea, and Barents regions. These events are often correlated with electronic-warfare operations, affecting civil aviation and maritime users who report repeated outages and falsified location reports (such as corrupted Automatic Identification System (AIS) and GNSS data).
- Regional Flashpoints: Intermittent but concentrated interference clusters are recorded in the Middle East, parts of South Asia, and specific Southeast Asian corridors. These events are linked to military activity or instances of criminal masking of vessel tracks.
- Localized Civilian Misuse: Lower-power, handheld jammers used by individuals (for privacy, to defeat trackers, or by illegal operators) create real, small-scale disruptions in urban areas, ports, or specific lanes across many countries.
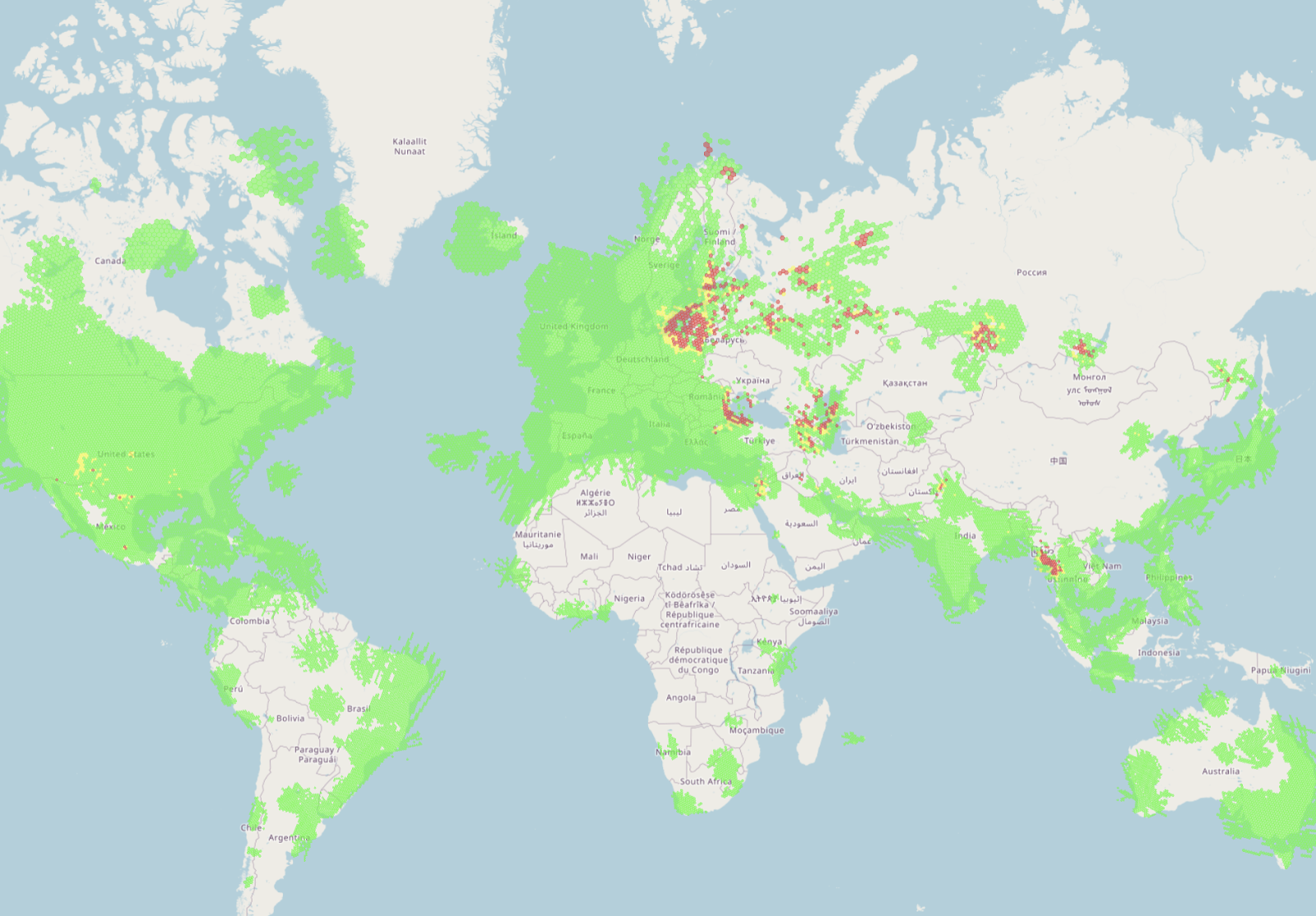
GPSJAM: Daily maps of GPS interference
In affected regions, independent investigative reports have documented sharp rises in interference incidents, with hundreds to thousands reported monthly between 2022 and 2025. For example, sustained interference impacting shipping and aviation in the Baltic Sea region has been attributed by Finnish authorities to coastal jamming operations.
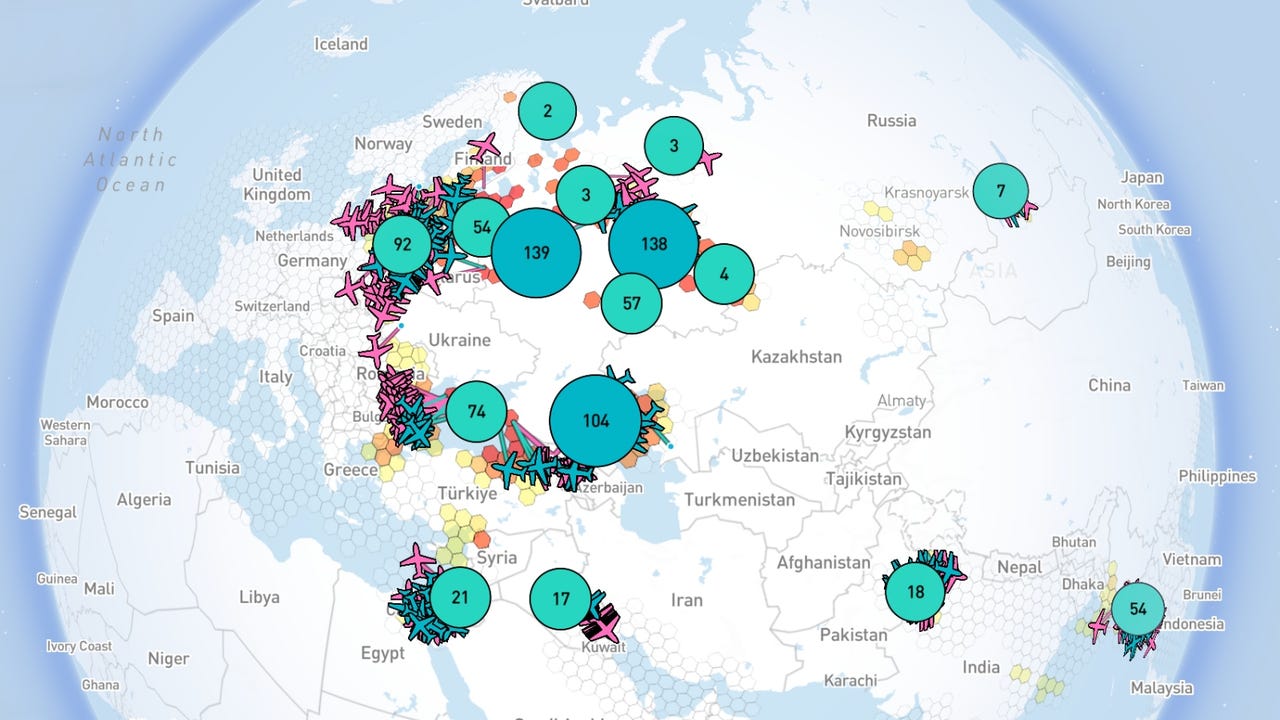
GPSWISE: GPS Spoofing & Jamming Map
Accessing Real-Time Interference Data and Spatial Monitoring
The geospatial community relies on accurate, timely monitoring. Several maintained portals offer live or near-real-time maps derived from dedicated sensors, crowd sources, and aircraft telemetry. These maps provide the best real-time window into the spatial extent of the phenomenon.
You can link to these platforms to follow the phenomenon:
-
- GPSJAM: Provides daily global maps built from ADS-B/aircraft performance, flagging areas with elevated GPS interference.
- Flightradar24: Features a specialized page that visualizes aircraft GPS accuracy anomalies on a global map with frequent updates.
- Stanford GNSS Interference Map: Offers a research-grade, interactive view showing detected jamming events and associated data resources.
- GNSS Interference Detection using ADS-B: Uses aircraft ADS-B telemetry to detect and visualize potential GNSS jamming or spoofing events on a global scale.
- GPSwise and SkAI’s Spoofing & Jamming Tracker: Platforms that combine ADS-B and other telemetry to flag possible spoofing or jamming affecting aircraft.
Note on Data Limitations: When incorporating these maps into analysis, it is essential to annotate their limitations: detection density often follows air traffic and receiver coverage, false positives can occur, and some advanced military events are intentionally concealed.
Case-studies
In the study “The Vulnerability of Inland Waterway AIS to GNSS Radio Frequency Interference,” the authors carried out lab and live-sky tests on an AIS receiver and found that jamming caused the vessel to completely disappear from other AIS screens, while spoofing made it appear in a false location. Meanwhile, the “GNSS Interference in the Baltic Sea” white paper documents 84 hours of GNSS disruption over a six-month campaign, primarily caused by jamming that degraded positional accuracy from 3–5 m to over 35 m. Together, these cases highlight that GNSS interference can lead not just to loss of signal, but to mis-located assets and corrupted spatial datasets—key concerns for any geospatial data user.
Geospatial Resilience: Practical Defenses for Data Users
Protecting PNT data integrity requires defenses operating at the receiver, system architecture, and procedural levels. For critical infrastructure and high-value remote sensing operations, consider the following technical mitigations:
1. Receiver and Antenna Measures
- Multi-Constellation and Multi-Frequency Receivers: Using satellites across systems (GPS, Galileo, GLONASS, BeiDou) and multiple frequency bands significantly raises the cost and complexity required for an attacker to achieve effective interference.
- Signal Authentication: The adoption of authenticated civil signals, such as Galileo OSNMA, enables receivers to cryptographically verify signal origin and integrity, materially raising the security bar against spoofing.
- Antenna Design: Using directional and adaptive antennas (Anti-Jam filters and antenna arrays) can suppress the power of local jammers or detect anomalous angle-of-arrival patterns consistent with a localized spoofing threat.
2. System and Architecture Resilience
- Alternative Timing and Fallback Sources: Critical systems must maintain system resilience via redundancy. This includes using holdover clocks (oscillators disciplined during GNSS availability) and integrating alternative time sources (e.g., PTP over fiber or eLoran where available) to reduce single-point failure risks.
- Integrity Monitoring and Cross-Checks: Implement monitoring functions like RAIM/ABAS-like integrity monitors. For mobile assets, cross-checking GNSS output against complementary sensors, such as Inertial Measurement Units (IMUs), odometry, or network-based location data, is vital to detect inconsistent GNSS outputs and trigger fail-safe modes before corrupted data is accepted.
3. Operational Awareness
- Operators should utilize the live maps listed above to avoid or react to current hotspots.
- Maintain open lines of communication with national GNSS service centers for timely incident reporting and advisories, which is critical for improved situational awareness.
Summary: Impact on geospatial data accuracy
When jamming or spoofing attacks target GNSS, the integrity of geospatial data is compromised in two ways. With jamming, the receiver may lose lock on satellites, resulting in missing or highly degraded position/time outputs. This can stop remote-sensing missions, derail timing networks, or corrupt positional metadata. Spoofing is even more insidious because the receiver continues to deliver a (false) position or time. For geospatial practitioners, this means: imagery or sensor data stamped with incorrect coordinates or times, mapping layers misaligned, navigation or surveying assets reporting wrong locations, or networks relying on accurate timing drifting unnoticed. Even if the error is small, accumulation of mis-located features or mis-timed events can lead to incorrect analyses (for example, in change detection, precision agriculture, infrastructure monitoring).
Did you like the article? Read more and subscribe to our monthly newsletter!










